Fast Track : 10 Months
Schedule: Monday, Wednesday, Friday
18h00 to 21h00-
13 June 2025
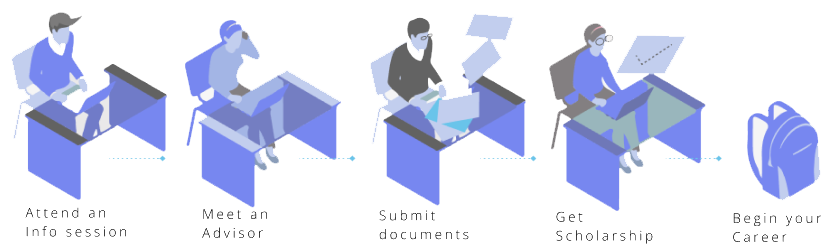
Mode of Delivery: Hybrid & Online Attend an Info Session
March 18th
6PM-7PM
Online
OVERVIEW
This course is designed to equip you with the essential skills and knowledge needed to defend digital assets in the ever-changing landscape of cyber threats.
Emphasizing a comprehensive cybersecurity program, the course covers infrastructure security and network/system protection. Delve into specific areas such as Threat Identification and Mitigation, Software Security, and Continuous Monitoring and Defense for a deep exploration of responsibilities, techniques, and strategies. Explore the significance of innovation in cybersecurity, gaining insights into cutting-edge solutions. Provide robust protection for digital assets in the evolving cyber threat landscape.
- See if you Qualify
- Talk to an Advisor
COURSE OUTLINE
Security
Download OutlineThis course introduces beginners to the fundamentals of networking, teaching the basics of connecting computers and devices. You will learn about IP addresses, routers, switches, and security protocols, which are essential for building and managing a network. The course will help you understand how data travels across networks and how to troubleshoot common network issues.
This course covers the essentials of IT infrastructure, focusing on cloud computing basics. You will explore how servers, storage, and networking are managed in the cloud, and gain an understanding of cloud service models like IaaS, PaaS, and SaaS. It's perfect for beginners looking to understand the backbone of modern IT environments.
In this course, beginners will learn programming and automation techniques to improve IT operations. You will work with scripting languages like Python to automate common IT tasks, such as system monitoring and data management, increasing efficiency and reducing manual errors.
This beginner-friendly course introduces the key principles of cybersecurity, teaching you how to protect networks, devices, and data from cyber threats. You'll explore topics like common attack methods, security protocols, and risk management. It's perfect for anyone interested in understanding the essentials of securing digital systems.
This course covers the essentials of securing networks and managing firewalls to prevent unauthorized access. You'll learn how to set up and manage firewalls, secure network traffic, and monitor networks for potential threats, ensuring a safe and protected network environment.
In this course, you'll learn how to detect cyber threats, respond to security incidents, and conduct forensic investigations. It covers identifying breaches, collecting evidence, and using incident response frameworks to mitigate damage and recover from attacks.
This course focuses on securing cloud environments and applications. You'll learn how to protect cloud-based data, implement secure application development practices, and manage risks in cloud infrastructure, ensuring your applications and data are safe from cyber threats.
This course provides guidance on how to build and advance your career in cybersecurity. You'll learn how to craft a strong resume, prepare for interviews, and explore various career paths in cybersecurity, helping you stand out in the competitive job market.
In this hands-on project, you'll apply your cybersecurity knowledge to solve real-world problems. You'll work on securing systems, responding to simulated cyberattacks, and managing security tools, gaining practical experience in handling cybersecurity challenges.
Become ready for the workplace
These MCIT programs helps you to be job ready.
NETWORK EVENTS
The Intelligent Networking Networking with companies Instructors sharing their network Peer to peer networking Meet with recruiters.
Resume is the key to making the first impact with your profile.
INTERVIEW PREPARATION
Resume building, LinkedIn Training, Mock interviews hosted by companies, Technical interview prep, Behavioral interviews.
We assist you turn your projects into relevant portfolios.
PORTFOLIO PREPARATION
Turn your projects into a portfolio Portfolios tell your story Relevancy of the projects display experience.
Mentorship & guidance - the key to career success.
MENTORSHIP
The Mentors, instructors, or alumni help you understand the required skills for your desired career path and the path to land your dream job!
WHO SHOULD APPLY?
If you want to become any of the following
Security Analyst | Security Administrator | Security Operations Center (SOC) Analyst | Cloud Security Engineer | Security Architect | Cloud Security Consultant | Cloud Developer | Cloud Tester | Speak to an advisor to determine eligibility.

Sihame B
BI Developer, Groupe Touchette

Mario A
BI Developer, National Bank, Canada

Aasma Lit M
BI Developer, Montreal College

Olga Zamora D
BI Analyst, Industrial Alliance, Canada
Admissions Process
The admission process entails the submission of several key documents. Applicants must provide their diploma and transcripts
- Highest level of education.
- Current resume detailing professional and education
- Birth certificate translated into either English or French
- 2 Photo identification are necessary
Upon successful completion the college grants the student an AEC (Attestation d’études collégiale)
Networking and Technical Support LEA.CL: Profile Security
-900 hrs-
INSTRUCTOR SPOTLIGHT

Sami Islam
Sami Islam has 10+ years of experience in the IT and Consulting Industry, specializing in comprehensive Cloud solutions. With expertise in Agile Methodology, he has led numerous Cloud Transformation projects, including migration, CI/CD Pipeline automation, and Data Warehousing solutions. Sami holds multiple certifications, including Google Cloud Professional Cloud Architect, AWS Solutions Architect Associate, and Azure Certifications.
Germán A. Torres
Germán, a dedicated Frontline Enablement Lead at Google, brings over 10 years of valuable experience to his role. As an accomplished engineer, entrepreneur, and technology enthusiast, he possesses an unwavering passion for work, applied sciences, and cutting-edge product design. Germán's visionary mindset led him to establish Rumbo Mobile Inc., a pioneering company that is dedicated to revolutionizing the parking marketplace with its innovative solutions.Loans & Scholarships
Scholarships for New Graduates
Students who have graduated with a post secondary diploma or degree from a qualifying institution in the last two years.
Scholarships for New Immigrants
Students who have arrived in Canada two years or less at the time of submitting their application
Merrit based Scholarships
The Montreal College of Information Technology offers merit-based scholarships to deserving candidates,for exceptional academic or professional contributions.
Other Options
We also have scholarships
for students who were laid off recently
in the past 6 months.
Empower students through Financial Aid
Conveying our commitment to student success through financial support.
Loans through the Government
Apply with the government to get financial aid through the AFE loan program (Aide financière aux études/Student financial assistance).
Loans from Partners
Our financial partners offer loans and personalized support to local entrepreneurs and internationally trained professionals.
Application Advice
Our financial partners offer loans and personalized support to local entrepreneurs and internationally trained professionals.

CALENDAR
Registration deadline:
For international students, it is highly recommended to register three months before the starting date. Talk to one of our advisors for more details about the registration process.
— F.A.Q —
We offer comprehensive cybersecurity courses covering topics of comptia security+ such as threat detection, ethical hacking, risk management, cryptography, secure coding practices, and incident response along with cloud security concepts.
Yes, our programs are designed to accommodate students with varying levels of expertise, including beginners. Our instructors and courses tailored for beginners to provide a solid foundation with varying levels of expertise.
A basic understanding of computer systems and networking concepts is recommended.
To be eligible for a program of study leading to an attestation of college studies (AEC), Student must have training deemed sufficient by the college and meet one of the following conditions:
- Have interrupted your full-time studies or pursued full-time post-secondary studies for at least 2 consecutive sessions or one school year;
- Be covered by an agreement concluded between the college and an employer or benefit from a government program;
- Have interrupted your full-time studies for one session and have pursued full-time post-secondary studies for one session;
- Hold a professional studies diploma.
- The program of study makes it possible to acquire technical training in a field for which there is no program of study leading to a college diploma;
- The study program is covered by an agreement concluded between the Minister and a department or agency of the Government of Québec regarding training.
Student must meet all the following requirements:
- Knowledge of computer hardware and Operating Systems like Windows, MacOS.
- Advanced High School mathematics
- Good to have knowledge on programming language & networking concepts
Our programs utilize a combination of lectures, hands-on lab exercises, case studies, and real-world projects to ensure a comprehensive learning experience. We also provide access to online resources and support forums for additional learning.
Yes, we facilitate internships and practical experience opportunities with industry partners to help students apply their skills in real-world scenarios and gain valuable experience.
Graduates of our programs can pursue various career paths including network administrator, cloud architect, cybersecurity analyst, system engineer, IT consultant, and more. Our career services team provides guidance and support for job placement and advancement.
Yes, we offer flexible study options including part-time evening classes and online courses to accommodate students with busy schedules or those unable to attend in person.